Check out our latest products
The head of security advocacy at Datadog, a cloud-based monitoring and analytics platform, has urged enterprises in Australia and the APAC region to accelerate phasing out long-lived credentials for popular hyperscale cloud services, warning that they remain a serious data breach risk.
Speaking with TechRepublic, Andrew Krug highlighted findings from Datadog’s State of Cloud Security 2024 report, which identified long-lived credentials as a persistent security risk factor. While credential management practices are improving, Krug noted they are not advancing as quickly or effectively as needed to mitigate risks.
Long-lived credentials are still a big threat to cloud security
The report revealed that nearly half (46%) of organisations using AWS rely on IAM users for human access to cloud environments — a practice Datadog called a form of long-lived credential. This was true even for organisations using centralised identity management to grant access across multiple systems.
Moreover, nearly one in four relied solely on IAM users without implementing centralised federated authentication. According to Datadog, this highlights a persistent issue: while centralised identity management is becoming more common, unmanaged users with long-lived credentials continue to pose a significant security risk.
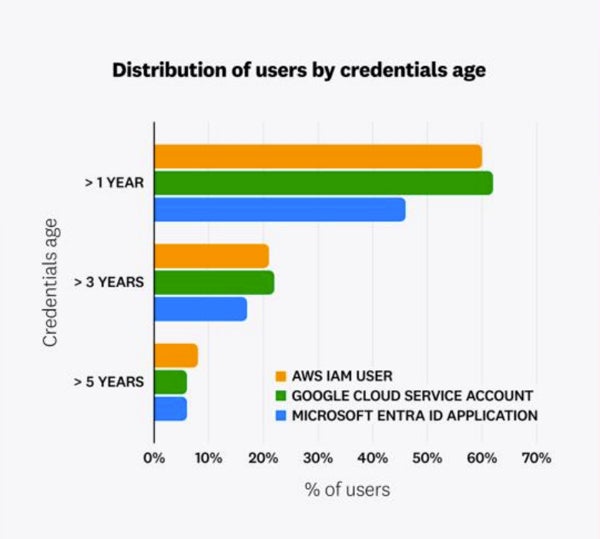
The prevalence of long-lived credentials spans all major cloud providers and often includes outdated or unused access keys. The report found that 62% of Google Cloud service accounts, 60% of AWS IAM users, and 46% of Microsoft Entra ID applications had access keys that were more than a year old.
Long-lived credentials come with a significant risk of data breaches
Long-lived cloud credentials never expire and frequently get leaked in source code, container images, build logs, and application artifacts, according to Datadog. Past research conducted by the company has shown they are the most common cause of publicly documented cloud security breaches.
SEE: The top five cybersecurity trends for 2025
Krug said there is mature tooling in the market to ensure secrets do not end up in production environments, such as static code analysis. Datadog’s report also notes the rise of IMDSv2 enforcement in AWS EC2 instances, an important security mechanism to block credential theft.
There are less long-lived credentials, but change is too slow
There have been moves to mitigate the problem, such as AWS launching IAM Identity Centre, allowing organisations to centrally manage access to AWS applications. While companies are in the process of changing to the service, Krug said, “I just don’t know that everyone considers this their highest priority.”
“It definitely should be, because if we look at the last 10 years of data breaches, the primary theme is that long-lived access key pairs were the root cause of those data breaches combined with overly permissive access,” he explained. “If we eliminate one side of that, we really substantially reduce the risk for the business.”
The long-lived credentials problem isn’t exclusive to APAC — it’s a global issue
According to Krug, APAC is no different from the rest of the world. With no regulation to control the management of long-lived credentials in the cloud in any particular jurisdiction, companies worldwide use similar approaches with similar cloud providers, often across multiple global jurisdictions.
What is stopping the move away from long-lived credentials?
The effort required to transition teams to single sign-on and temporary credentials has slowed the adoption of these practices. Krug said the “lift and shift” involved in migrating development workflows to single sign-on can be considerable. This is partly due to the mindset shift required and partly because organisations must provide adequate support and guidance to help teams adapt.
However, he noted that tools like AWS Identity Centre, which has been available for three years, have made this transition more feasible. These tools are designed to reduce developer friction by streamlining the authentication process, minimising the need for repeated MFA sign-ins repeatedly, and ensuring that workflows remain efficient.
SEE: How AI is amplifying the risks of data in the cloud
“AWS Identity Centre is a great product and enables these very seamless user flows, but folks are still midstream in migrating to it,” Krug said.
What should you do with your long-lived credentials?
Datadog’s report warned that it is unrealistic to expect that long-lived credentials can be securely managed. The vendor recommends that companies adopt secure identities with modern authentication mechanisms, leverage short-lived credentials, and actively monitor changes to APIs that attackers commonly use.
“Organisations should leverage mechanisms that provide time-bound, temporary credentials,” the report said.
Workloads. For workloads, Datadog said this end can be achieved with IAM roles for EC2 instances or EKS Pod Identity in AWS, Managed Identities in Microsoft Azure, and service accounts attached to workloads for Google Cloud if the organisation uses the major global hyperscalers.
Humans: For human users, Datadog said the most effective solution is to centralise identity management using a solution like AWS IAM Identity Center, Okta, or Microsoft Entra ID and avoid using individual cloud users for each employee, which it labelled “highly inefficient and risky.”


![[5G & 2.4G] Indoor/Outdoor Security Camera for Home, Baby/Elder/Dog/Pet Camera with Phone App, Wi-Fi Camera w/Spotlight, Color Night Vision, 2-Way Audio, 24/7, SD/Cloud Storage, Work w/Alexa, 2Pack](https://m.media-amazon.com/images/I/71gzKbvCrrL._AC_SL1500_.jpg)



![[3 Pack] Sport Bands Compatible with Fitbit Charge 5 Bands Women Men, Adjustable Soft Silicone Charge 5 Wristband Strap for Fitbit Charge 5, Large](https://m.media-amazon.com/images/I/61Tqj4Sz2rL._AC_SL1500_.jpg)