Check out our latest products Image: Ferran Rodenas/Flickr/Creative Commons If you use VMware Tools for Windows, it is critical to update to ...
Check out our latest products Phishing takes advantage of the weakest link in any organization’s cybersecurity system — human behavior. ...
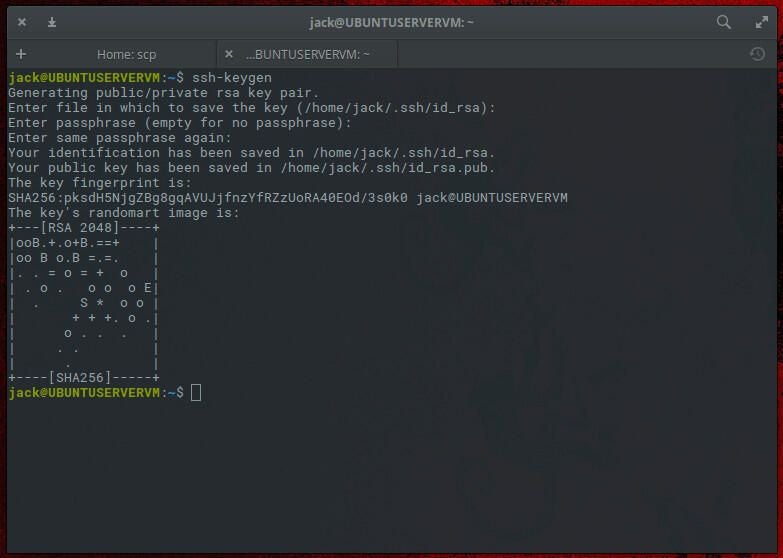
Check out our latest products Anyone who administers Linux machines likely knows secure shell. Without this tool, administering those ...
Check out our latest products Every convenience you offer your customers creates a potential vulnerability that a hacker could exploit. ...