Check out our latest products - Advertisement - The controllers use strong cryptography in hardware to help systems stay safe from future attacks ...
Check out our latest products Modern enterprises are adopting AI applications, particularly generative AI (GenAI), at a rapid rate. This ...
Check out our latest products In the era of interconnected devices, securing IoT systems is paramount to protect sensitive data from ...
Check out our latest products KeePass fast factsOur rating: 3.0 stars out of 5Pricing: FreeKey featuresDownloadable user-generated ...
Check out our latest products This Motorola Moto G Power 5G shows the midnight blue color option. Image: Amazon New Android malware is using ...
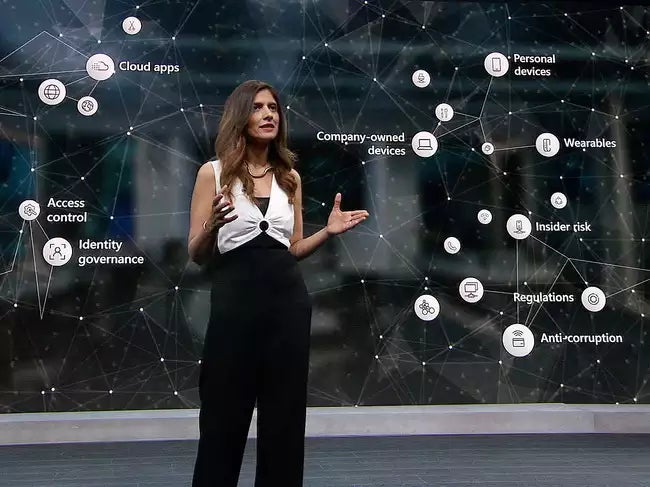
Check out our latest products Vasu Jakkal, corporate vice president, Microsoft Security. Image: Microsoft Microsoft is raising the bar in ...
Check out our latest products Image: cynoclub/Envato Elements Apache Tomcat is under attack as cybercriminals actively exploit a recently ...
Check out our latest products Image: Wiz Google has announced it is acquiring cybersecurity startup Wiz for $32 billion. The acquisition is ...
Check out our latest products Dashlane fast factsOur rating: 4.4 stars out of 5Pricing: Starts at $4.99 per monthKey featuresSecure ...
Check out our latest products Key Takeaways Point-of-sale (POS) security operates through a combination of hardware and software ...
- 1
- 2
- 3
- …
- 5
- Next Page »